Biobanks often store patient (PHI) data, which is confidential and legally protected. If the data is not stored securely it will pose a serious business risk that can invoke lawful action, such as the Singapore Patient Data Breach in 2018.
This article is written based on our implementation experience at the University of New South Wales biorepository.
To ensure data privacy and minimize data vulnerability, Krishagni provides an option to encrypt the OpenSpecimen MySQL database “at rest”, which will ensure that if anyone with malicious intent gets access to the server will not decrypt the data.
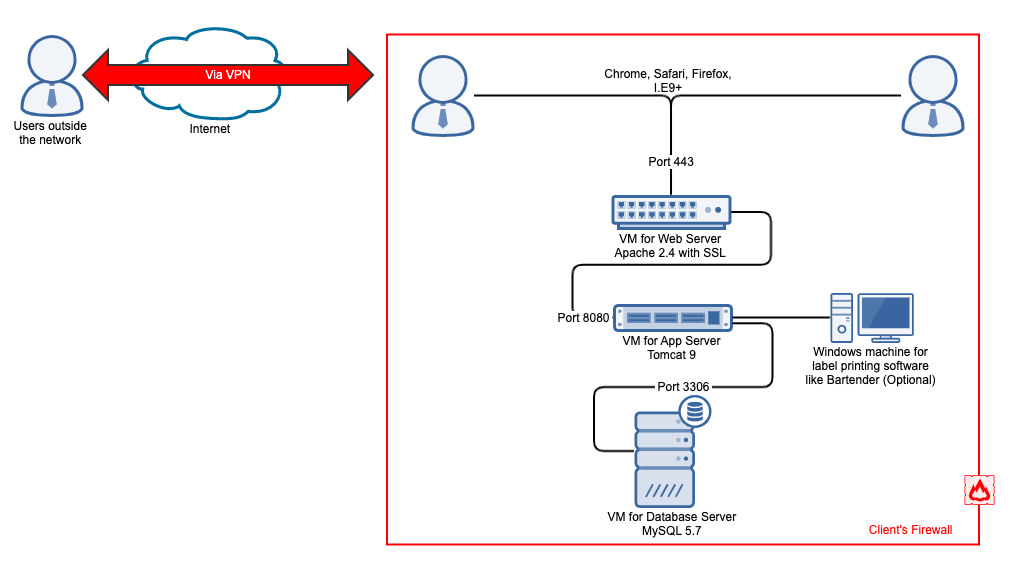
Below is a typical network diagram of OpenSpecimen deployment. Usually, on-premise deployments are safer than on-cloud deployments since the database is deployed within the institute’s VPN. However, when the database is on the cloud, it is vulnerable to attacks.
There are two types of data encryption:
At rest: In the database, all the patient’s data is stored in files. The attacker can retrieve sensitive data if they get direct access to these files. To avoid this, we can encrypt these data files in such a way that even if someone gains access to the data files, they cannot access the data.
In transit: When data transfers through a network, it can be intercepted before it reaches the target system. It is also known as “Man In The Middle” attack. To prevent this, the data during transit is encrypted using SSL encryption.
MySQL Database Encryption
The MySQL database can be encrypted using the “Keyring Plugin” provided by MySQL.
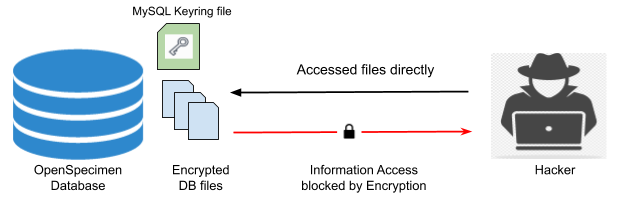
MySQL provides the keyring plugin to encrypt the table data files. To encrypt and decrypt database keyring files is used. This file should be kept outside of the database server file system, i.e., on any external hard drive or remote server for more security.
While this article is written for MySQL, the same can be achieved with other databases like Oracle. Post encryption, we have not experienced any performance (speed) drop in the OpenSpecimen application.
Written by: Krishna Waidande. Krishna is a System Administrator at OpenSpecimen and manages product deployments, databases and configuration.
For more details email [email protected]
